Den folgenden Artikel gibt es leider nur in Englisch!
Some time ago I read a book about kernel and userland rootkits. As I dont have alot of freetime I want to get started trying hooks in userland and not in the windows kernel using drivers. (And of course I dont wanted my pc to crash by bluescreens)
What do we need for userland detour/inline hooking?
– Target process or DLL
– An explicit memory address with a function call for the hook (can be dynamically)
– An application which injects our patch dll into the target object
– And of course the patching dll itself
My aim was to hide processes in the taskmanager of windows 2000. Therefore I had to find the native API functions to query a list of processes. After some hours in ollydbg I found ‚ZwQuerySystemInformation‘ as a solution to my problem in ntdll.dll. This native API function is the one who will run the kernel gate switch via interrupts. So if we hook this function we can filter the whole in- and output of it – exactly that what I wanted.
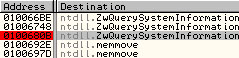
To automate this hooking process I wrote an application which:
1. Enumerates all processes
2. Searches for ‚taskmgr.exe‘
3. Opens this process via ‚OpenProcess‘ + some additional needed stuff
4. And loads the dll as a remote thread into ‚taskmgr.exe‘
The target dll which will patch the ‚ZwQuerySystemInformation‘ function now gets active in DllMain():
1. Start a new thread so the dll doesnt gets unloaded after our injection app has quit
2. Open the process where the dll is loaded in (taskmgr.exe in this example)
3. Find a handle to ntdll.dll and the memory address of ‚ZwQuerySystemInformation‘
4. Enable write access to this memory page
5. Write our jump + the address of the detour function of our dll into memory
From now, if taskmgr.exe will call ‚ZwQuerySystemInformation‘ over the overlayed functions of the API, our detour function will be called instead the original code. In this new jump we set a memory address which belongs to an selfmade filter function who does the rest:
1. Backup all registers and the stack
2. Run the kernel gate switch via interrupt
3. Filter the returned informations
4. And give the control back to the taskmgr.exe code
![]()
Thats all 🙂 Isn’t that easy?
If you want you can download the whole project and code here.
The filter function in the code isnt finished yet but I think its not a problem for you to finish this up 😉